NEW YORK — A joint investigation between Access Now, CyberHUB-AM, the Citizen Lab at the Munk School of Global Affairs at the University of Toronto (the Citizen Lab), Amnesty International’s Security Lab, and an independent mobile security researcher Ruben Muradyan, has uncovered hacking of civil society victims in Armenia with NSO Group’s Pegasus spyware.
Israel’s NSO Group became the center of controversy after an international media consortium in July 2022 reported that its Pegasus spyware was used in attempts to hack smartphones belonging to more than a dozen current or former world leaders, journalists, human rights activists, and executives in some 50 countries.
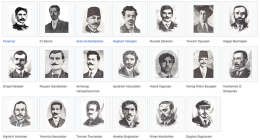
The investigation has identified 12 individuals whose Apple devices were targeted with Pegasus spyware at various times between October 2020 and December 2022.
According to Access Now, the victims include Kristinne Grigoryan, the former human rights defender in Armenia; Karlen Aslanyan and Astghik Bedevyan, two journalists from Radio Free Europe/Radio Liberty (RFE/RL) Armenian service; two unnamed United Nations officials; Anna Naghdalyan, a former spokeswoman for the Armenian Ministry of Foreign Affairs (now an NGO employee); as well as activists, media owners and academics.
In the case of Armenia’s top human rights defender Grigoryan, Access Now said her phone was infected “soon after she shared her phone number with her Azerbaijani counterpart.”
Circumstantial evidence suggests that the targeting is related to the military conflict in the Republic of Artsakh. This is the first documented evidence of the use of Pegasus spyware in an international war context.
The investigation began after Apple sent its first wave of notifications to their users in November 2021, warning them that they may have been targeted with state-sponsored spyware.
NSO Group claims that their technology is exclusively sold to governments, which is broadly consistent with past findings by research groups and investigative journalists. The researchers believe that this operation is the work of a governmental Pegasus customer.
Neither Access Now nor the technical partners at the Citizen Lab and Amnesty International conclusively link this Pegasus hacking to a specific governmental operator. The targeting occurred during the Azerbaijan-Armenia conflict, and the Armenia spyware victims’ work and the timing of the targeting strongly suggest that the conflict was the reason for the targeting.
Substantial evidence exists, meanwhile, to suggest that Azerbaijan is a Pegasus customer, and the targets would have been of intense interest to Azerbaijan, the report says.
Pegasus has been used extensively in Azerbaijan to target a wide range of journalists, civil society and political opposition figures. The Pegasus Project revealed that over 1,000 Azerbaijani numbers were selected for targeting by a Pegasus government customer. Amnesty International’s Security Lab has since forensically confirmed that at least five members of Azerbaijani civil society had their devices infected with Pegasus between 2019 and 2021.